
Security Tips for Apache Webserver
Apache was the most popular open source webserver available for Linux until recently. As of writing this Apache is used by 31.3% of all websites according to W3Techs. In the words of Apache.org,
The Apache HTTP Server has a good record for security and a developer community highly concerned about security issues.
Source
Needless to say, Apache webserver is highly matured when it comes to security of the core server. Given its ease of use, it is easy to configure it for better security. Today I’ll share some tips for securing an default Apache Webserver installation. Before proceeding further I assume you’ve a working installation of Apache Webserver running.
1. Keep Apache Updated
Keeping software updated is needless to say one of the most wide spread advice given by security experts. Software updates not only improve security of software but also sometimes improve the performance greatly and provide new features. So, it is highly recommended to keep Apache updated with the latest patches whenever possible. Sometimes it is possible that you’re not available to patch the security vulnerabilities when the patches are out and your server may get exploited. If you’re like me and have a very busy life, then I recommend adding a cron job to your Ubuntu server as the root user to keep all your software updated every 12 or 24 hour. To update every 24 hours you can add the following code to your crontab:-
1 0 * * * apt update && apt upgrade -y && apt autoremove -yWhat the above entry does is it runs the software update of installed packages everyday at 12.01 AM.
2. Hide Apache version and OS information
On a default installation, Apache webserver shows its version and OS information in headers and error pages. You can get this information by simply visiting a non existing page or with a curl command.
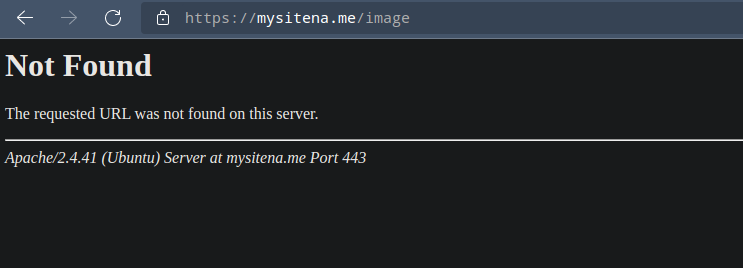
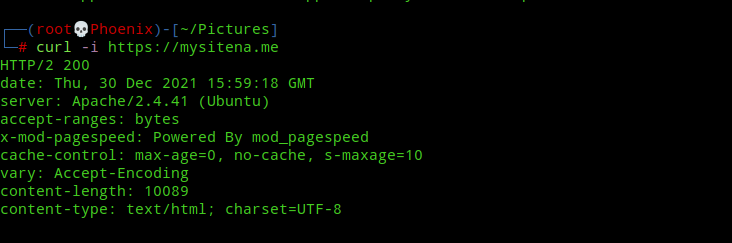
To prevent Apache from showing this information edit /etc/apache2/conf-available/security.conf and change the following values:-
ServerTokens OS
ServerSignature Onto
ServerTokens Prod
ServerSignature OffAfter changing the above lines restart Apache server with the following command:-
systemctl restart apache2Now again try to visit a non existing page or use curl to get headers and you’ll see that the version and OS information won’t show up.
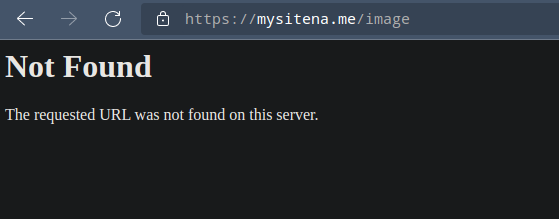
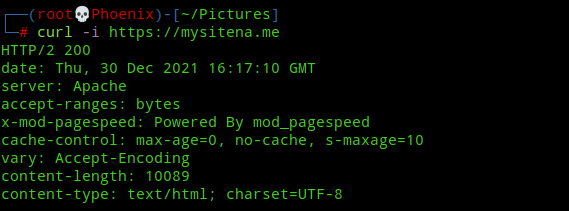
Note:- If you’ve installed and enabled Apache mod-security module, then you can edit /etc/apache2/conf-available/security.conf and add “SecServerSignature <your value>” to the file, where <your value> can be any random string of your choice which will replace the “Apache” value in the above image.
3. Run software with a separate user on Apache server
Running software with the default Apache user can lead to compromise of all hosted software in case of a multi site install. For e.g, if your WordPress installation is compromised, then the attacker/hacker can get full access to all other webapps running on the server if the default Apache user is used to run all of them. If you’re running PHP-FPM in your server, then you can refer to this guide by me on how to use privilege separation for multisite installs. A similar user separation concept can be applied to software other than PHP running on Apache as well.
4. Disable HTTP Trace method
According to Apache.org,
The default
TraceEnable onpermitsTRACErequests per RFC 2616, which disallows any request body to accompany the request.TraceEnable offcauses the core server andmod_proxyto return a405(Method not allowed) error to the client.
If you want to get more information on how this configuration can be used to exploit your server, then you can visit this page by PortSwigger Academy to learn more. For a better explanation of the lab provided by them, you can visit my walkthrough to get an idea how dangerous it can be. To disable this configuration edit /etc/apache2/conf-available/security.conf and change the TraceEnable configuration to :-
TraceEnable offand restart Apache webserver with:-
systemctl restart apache25. Disable Directory Listing
On a default installation Apache will list the contents of the webroot if there is no index file, for e.g, index.html present. To prevent Apache from directory listing add the following code snippet to your /etc/apache2/apache2.conf and restart Apache:-
<Directory /path/to/your/webroot>
Options -Indexes
</Directory>Note:- Replace /path/to/your/webroot with the actual path to your webroot where your webapp/site is installed.
6. Use Secure SSL configuration
According to Mozilla SSL Configuration Generator, a Modern configuration has services with clients that support TLS 1.3 and don’t need backward compatibility. But for most general-purpose servers an Intermediate configuration is recommended where only TLS 1.2 and 1.3 is used. While installing a SSL certificate on your Ubuntu server I recommend using a Intermediate configuration like the one below generated from Mozilla SSL Configuration Generator.
# generated 2021-12-30, Mozilla Guideline v5.6, Apache 2.4.41, OpenSSL 1.1.1k, intermediate configuration
# https://ssl-config.mozilla.org/#server=apache&version=2.4.41&config=intermediate&openssl=1.1.1k&guideline=5.6
# this configuration requires mod_ssl, mod_socache_shmcb, mod_rewrite, and mod_headers
<VirtualHost *:80>
RewriteEngine On
RewriteCond %{REQUEST_URI} !^/\.well\-known/acme\-challenge/
RewriteRule ^(.*)$ https://%{HTTP_HOST}$1 [R=301,L]
</VirtualHost>
<VirtualHost *:443>
SSLEngine on
# curl https://ssl-config.mozilla.org/ffdhe2048.txt >> /path/to/signed_cert_and_intermediate_certs_and_dhparams
SSLCertificateFile /path/to/signed_cert_and_intermediate_certs_and_dhparams
SSLCertificateKeyFile /path/to/private_key
# enable HTTP/2, if available
Protocols h2 http/1.1
# HTTP Strict Transport Security (mod_headers is required) (63072000 seconds)
Header always set Strict-Transport-Security "max-age=63072000"
</VirtualHost>
# intermediate configuration
SSLProtocol all -SSLv3 -TLSv1 -TLSv1.1
SSLCipherSuite ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384
SSLHonorCipherOrder off
SSLSessionTickets off
SSLUseStapling On
SSLStaplingCache "shmcb:logs/ssl_stapling(32768)"
7. Disable unnecessary modules
By default Apache enables a lot of modules and any extra module that we don’t need can pose a security risk for our server and serve as a path for an attacker to get into our server. You can verify all the modules loaded by Apache with the following command:-
apache2 -M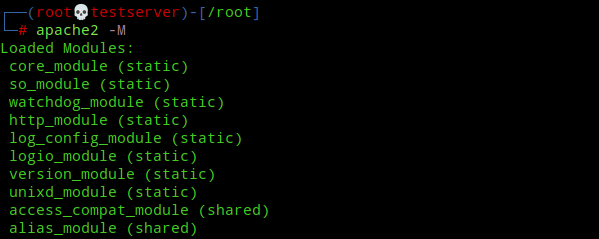
Next you can disable any unwanted modules with the following command:-
a2dismod <module name> <module name> ...8. Restrict access to Server files
To make sure that files and folders outside webroot are not accessible by clients we’ve to restrict access with “Allow” and “Deny” options in /etc/apache2/apache2.conf. For e.g, to secure the root directory of our server from outside access add the following code snippet to /etc/apache2/apache2.conf :-
<Directory "/">
Require all denied
</Directory>The above configuration will prevent any malicious client from walking through the entire filesystem. Further, it is highly recommended to add the following line to your Apache configuration files to prevent access to server root directory:-
UserDir disabled rootNote:- The above line expects the apache userdir module to be active. You can use “a2enmod userdir” command to activate the userdir module.
9. Disable .htaccess file and prevent its usage
According to Apache.org,
In general, you should only use
.htaccessfiles when you don’t have access to the main server configuration file. There is, for example, a common misconception that user authentication should always be done in.htaccessfiles, and, in more recent years, another misconception thatmod_rewritedirectives must go in.htaccessfiles. This is simply not the case.
A .htaccess file can be used to override server configuration and allowing users to create it can pose a potential security risk as this file can be used to bypass security features you’ve implemented. Also, a .htaccess file can slow down an Apache server. According to Apache.org,
You should avoid using
.htaccessfiles completely if you have access to httpd main server config file. Using.htaccessfiles slows down your Apache http server. Any directive that you can include in a.htaccessfile is better set in aDirectoryblock, as it will have the same effect with better performance.
Which is why I don’t use a .htaccess file for my website. To prevent .htaccess file from overriding your server configuration add the following code to /etc/apache2/apache2.conf:-
<Directory "/">
AllowOverride None
</Directory>This will prevent usage of .htaccess file server-wide and you’ll have the option to enable it for specific directories as needed.
10. Install a WAF
A WAF (Web Application Firewall) is a type of application firewall that monitors, filters and blocks HTTP traffic coming and going from a webapp. A WAF can protect your website against attacks like SQLi, XSS, CSRF, LFI/RFI. For e.g, ModSecurity is an open source, cross platform WAF engine for Apache and is free to use and can help prevent most basic web attacks known to mankind. ModSecurity also provides rule sets which can help in real time monitoring, logging and access control. To install Apache mod_security module module use the following command:-
apt install libapache2-mod-security2Next, restart Apache server:-
systemctl restart apache2By default no rules are enabled for mod_security so it won’t work unless we make some changes. Installing mod_security module creates a file with some default ruleset already configured. To create the mod_security configuration file use the following command:-
cp /etc/modsecurity/modsecurity.conf-recommended /etc/modsecurity/modsecurity.confNext, edit the /etc/modsecurity/modsecurity.conf file with your favourite text editor and change the line:-
SecRuleEngine DetectionOnlyto
SecRuleEngine OnNow, restart Apache server for the changes to take effect.
systemctl restart apache2And so, you’ve enabled a WAF with a default rule set.
11. Install mod_evasive
mod_evasive is a module for Apache that protects against DDoS(Distributed Denial of Service) attacks or brute force attacks. It is also designed to be a detection tool, and can be easily configured to talk to ipchains, firewalls, routers etc. I recommend this guide from Linode to install and test the mod_evasive module.
Conclusion
So these are my tips to secure Apache webserver. There are a few additional configuration changes you can do to secure you Apache server but I left them as these tips are mostly enough for the average user. For further reading you can refer this official guide on security from Apache.org. Have a nice day! 🙂