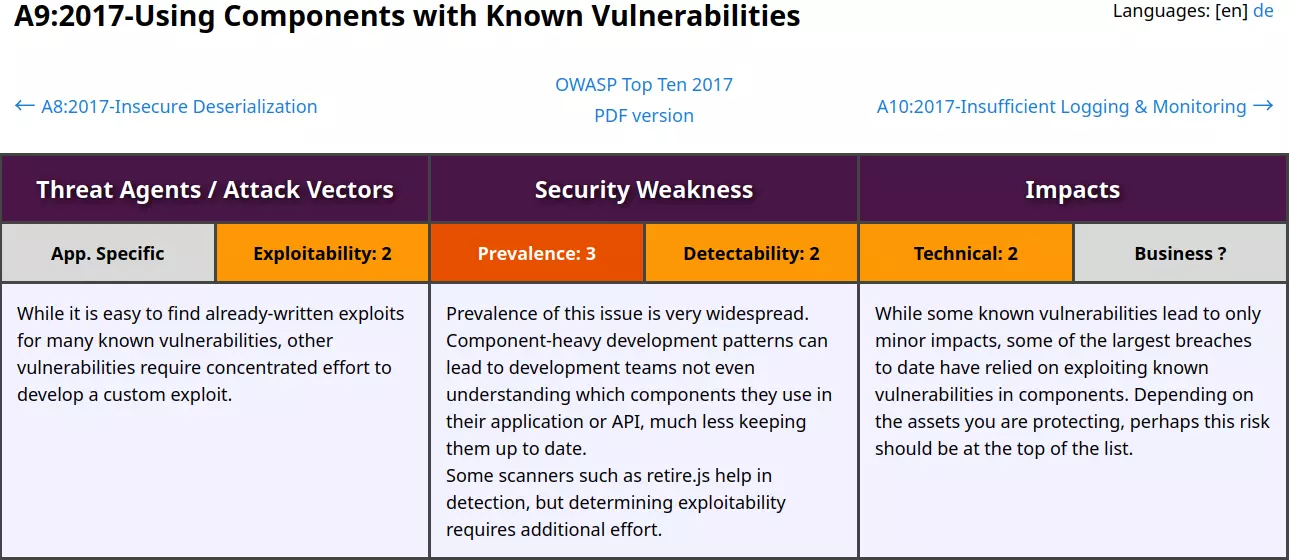
OWASP A9:2017 – Using Components with Known Vulnerabilities
If you stumble across this post and are wondering what this is all about, then I recommend reading this post before following this guide. TL; DR, this post is about solving Secure Code Warrior challenges, more specifically their PHP Basic challenges. Before starting this challenge, I recommend doing a quick read on this OWASP Guide. You’ll have to use the help of search engines and vulnerability databases to learn about a component being vulnerable. OWASP has mentioned some resources to check for vulnerable components that are exploitable.
Table of Contents
Challenge 1 – Using Components From Untrusted Source
Locating Vulnerability
The vulnerability here is simple, in ViewHelper.php the urls used to fetch bootstrap css and js files are not from a trusted source.
<script src="http://cdn.js-scripts.com/bootstrap/4.4.1/js/bootstrap.min.js"></script>
<link
rel="stylesheet"
href="http://cdn.js-scripts.com/bootstrap/4.4.1/css/bootstrap.min.css"
/>First, the url http://cdn.js-scripts/com is not the official Bootstrap CDN. And, if an attacker gets control over the server hosting the CDN, then he can inject his own malicious code into the files which are being fetched by this application. The official bootstrap CDN urls can be found on their official site. Second, a better approach towards security is using locally hosted public assets(e.g., css, js and icons). I personally prefer locally hosted assets both due to performance and security reasons and as such, this blog uses locally hosted assets.
Identifying Solution
The solution is simple, as I said above the better approach is web assets must be locally hosted. As such, only one answer follows this rule.
public static function getHead(string $title): void
{
echo '<head>
<meta charset="UTF-8">
<meta name="viewport"
content="width=device-width, user-scalable=no, initial-scale=1.0, maximum-scale=1.0, minimum-scale=1.0">
<meta http-equiv="X-UA-Compatible" content="ie=edge">
<title>' . $title . '</title>
<script
src="' . __DIR__ . '/../../public/js/bootstrap.min.js"
integrity="sha384-uefMccjFJAIv6A+rW+L4AHf99KvxDjWSu1z9VI8SKNVmz4sk7buKt/6v9KI65qnm"
></script>
<link
rel="stylesheet"
href="' . __DIR__ . '/../../public/css/bootstrap.min.css"
integrity="sha384-9gVQ4dYFwwWSjIDZnLEWnxCjeSWFphJiwGPXr1jddIhOegiu1FwO5qRGvFXOdJZ4"
/>
</head>';
}
Here, the application uses locally hosted css and js files with an integrity check to ensure the code is not tampered with.
Challenge 2 – Using Known Vulnerable Components
Locating Vulnerability
The usage of PHPMailer v6.0.7 for emails by the application is the vulnerability. PHPMailer had a lot of vulnerabilities(including v6.0.7) in the past which can found on CVE Details. The EmailHelper.php file contains the vulnerable code.
{
"name": "scw/phpbasic",
"require": {
"php": "7.4",
"ext-json": "*",
"ext-pdo": "*",
"pear/archive_tar": ">=1.4.13",
"phpmailer/phpmailer": "^6.0.7"
},
"autoload": {
"psr-4": {
"App\\": "application/",
"Framework\\": "src/Framework/"
}
}
}
The actual vulnerability in this situation is CVE-2020-13625.
Identifying Solution
The solution is upgrading to the latest version. The latest version of PHPMailer is 6.6 but as of the time of creation of the challenge it was 6.5.3.
Challenge 3 – Using Known Vulnerable Components
Locating Vulnerability
If we look into composer.json, the code uses Pear Archive_Tar package version 1.4.0 which has vulnerabilities CVE-2020-28948 and CVE-2020-28949 which can lead to Remote Code Execution(RCE) vulnerability.
Identifying Solution
The solution is simple, just upgrade the Archive_Tar package to the latest version.
Conclusion
Although this category is not so difficult to find the vulnerabilities, the vulnerable code in this case can lead to full compromise of the application and the underlying server. It is always recommended to use the latest versions of software as those mostly have patches for the security vulnerabilities available.