
Secure Code Warrior Challenges
Recently, I learned about Secure Code Warrior from a friend and was so much pleased with the service I felt that after spending money on so many Security Related Courses in the last few years, I finally found one that’s really worth subscribing to. Sadly, they don’t offer individual subscriptions.
Introduction
Secure Code Warrior is a training platform focused mainly on developers and appsec engineers. As such, it is a learning platform that teaches where and how you can find security bugs in your code that fall under the OWASP Top 10 Web Application Security Risks. The learning platform is built on an extensive library of content covering more than 50 language:framework-specific categories, including; Front-end Web, Mobile, Infrastructure-as-Code (IaC), Back-end and API’s.
The best thing about the platform is, the training is gamified and allows participants to earn points and collect Security badges as they play and reach higher levels. This helps one learn things in a fun and playful way.
About my experience
When I signed up for the platform I didn’t knew that an individual cannot have access to more than one language/framework from the same account if they don’t have a business or enterprise subscription(They don’t provide individual subscriptions at the moment). I signed up for the PHP Basic challenge and was really glad that I did. According to w3techs, close to 80% of the web runs on PHP, so it is the most important language to learn when it comes to web security. After playing the challenges, I learnt a lot about PHP code security auditing and where exactly to look in PHP code for potential vulnerabilities. I felt like it was a superfun way to learn about vulnerabilities in code. As such, I ended up with the PHP Security Champion rank(the highest level on the platform) with just 5 incorrect attempts! You can see my results by visiting this link.
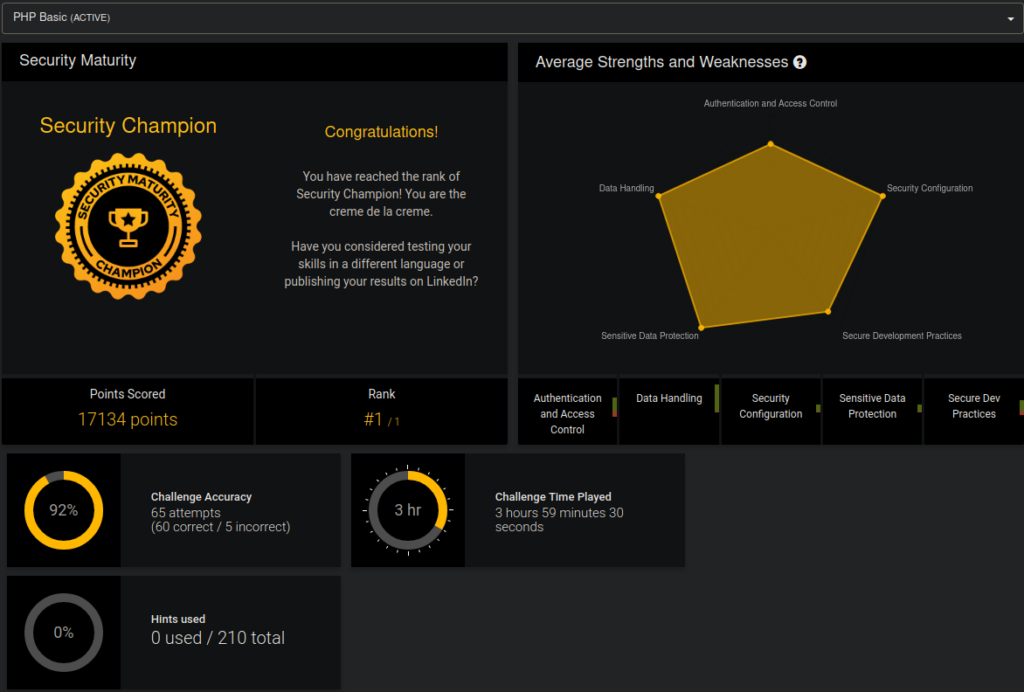
I’ve decided to share the methodology and process I used to finding security bugs in code provided in the challenges. As the PHP Basic language/framework doesn’t require a subscription, you can choose it to create a free account and then follow up with my guides. Also, before attempting any challenges feel free to refer the learning resources provided on the specific vulnerability from the resources section. By the time I finish this series, I’ll have covered all OWASP Top Ten 2017 attack vectors from a source code review perspective. In the future, I may even write about vulnerabilities in C# (.NET) and Python code if I get enough free time. It is going to be a fun journey for me writing about vulnerabilities in code. Hope you like them.